Twitter user @Stephen Lacy discovered a massive obfuscation malware attack on GitHub, with over 35,000 repositories currently affected, including well-known projects like crypto, golang, python, js, bash, docker, k8s, and more.
These malware attacks are very well disguised and look like innocuous commits with messages like "bump version to 0.3.11":
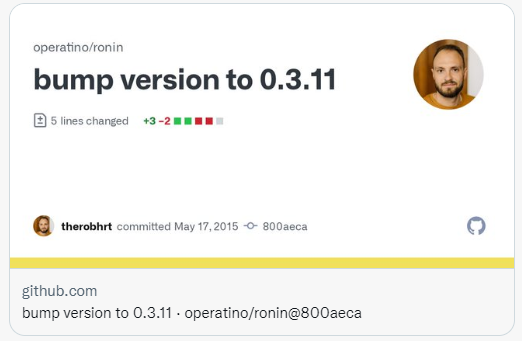
Some of them were confused into legitimate PRs, but the repository did not receive any PRs, instead every go file in the repository was infected:
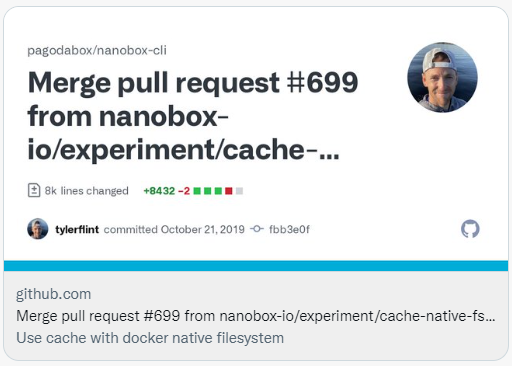
The history of some of these repositories includes a commit from the original author that was not verified by GPG, which means that the commit was forged by an attacker. In addition to the original author, the malware may also pretend to be other developers, but click on it and you will find that the user does not exist.
This part of the malicious attack is related to the vulnerability of GiuHub itself. For example, we reported earlier that Linus used the GitHub vulnerability to publish a mischievous README . The URL /blob/<faked_commit> publishes arbitrary commits.
These attacks send the entire ENV of scripts, applications, laptops (electron applications), etc. including account credentials such as security keys, AWS access keys, encryption keys, etc., to the attacker's server. Most of the malicious attack commits have been cleaned up so far, but new ones are still being made, and it is recommended that you use GPG to sign each commit.
Related Links: https://twitter.com/stephenlacy
END