linux_examples148 (20220804 )
refer to:
https://github.com/prometheus/blackbox_exporter
1. Preparation
1. The version of the package
prometheus-2.18.1.linux-amd64.tar.gz
blackbox_exporter-0.22.0.linux-amd64.tar.gz
2. I have access to the service managed by supervisord. The default is port 9115
cat /etc/supervisord.d/prometheus_blackbox_exporter.ini
[program:prometheus_blackbox_exporter]
command=nohup ./blackbox_exporter --web.listen-address=":9115"
directory=/root/ceph_monitor/blackbox_exporter
autostart=false
autorestart=true
stopwaitsecs=1
startsecs=3
user=root
stopasgroup=true
stdout_logfile=/root/ceph_monitor/blackbox_exporter/log/prometheus_blackbox_exporter.log
stderr_logfile=/root/ceph_monitor/blackbox_exporter/log/prometheus_blackbox_exporter.errlog
2. Deployment
1. Modify the configuration blackbox.yml
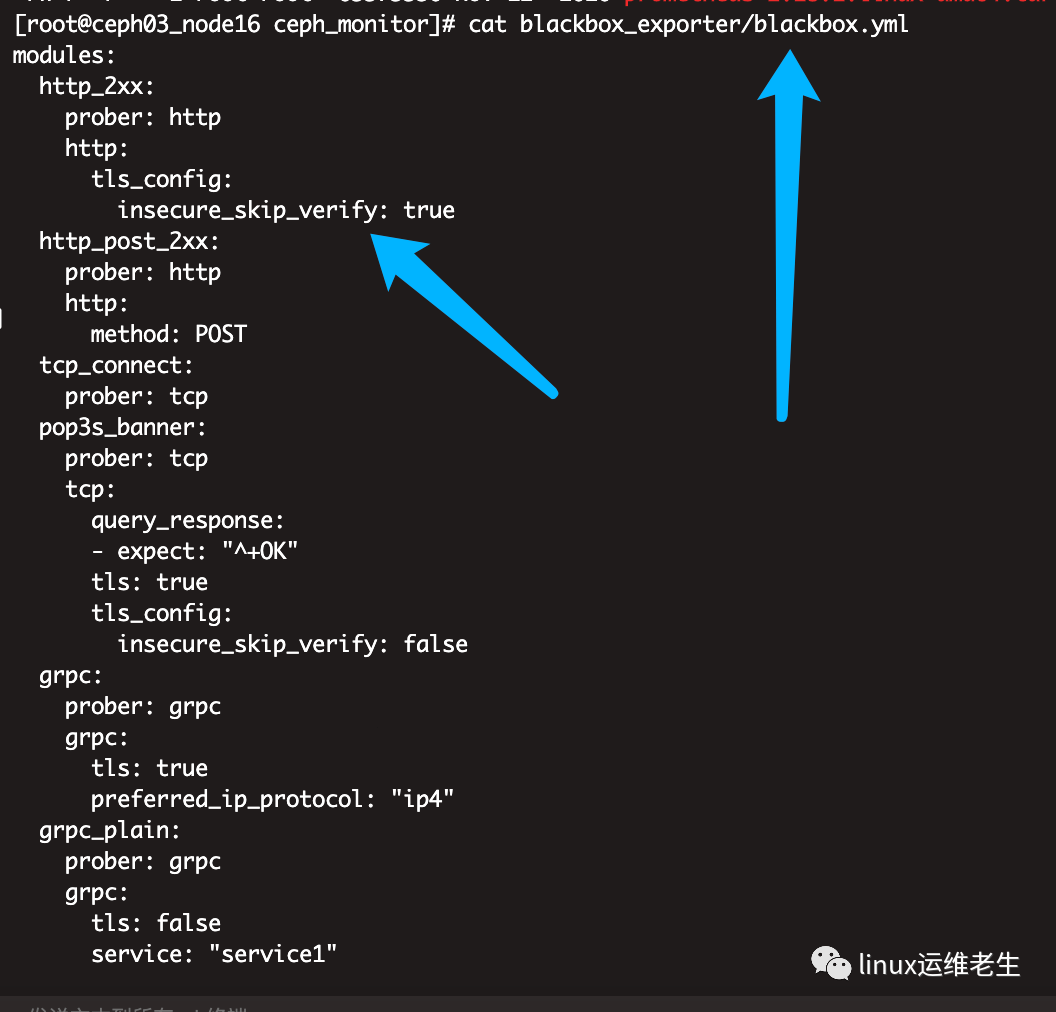
modules:
http_2xx:
prober: http
http:
tls_config:
insecure_skip_verify: true
Added the following three lines of information note format
http:
tls_config:
insecure_skip_verify: true
Modified configuration to resolve this error message
prometheus x509 certificate signed by unknown authority
2. Directly increase the job. The multiple sites of a site I provide here can be written together or separately
- job_name: 'zabbix_server'
metrics_path: /probe
params:
module: [http_2xx]
static_configs:
- targets:
- http://zabbix.mingmatechs.com/zabbix
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: 127.0.0.1:9115
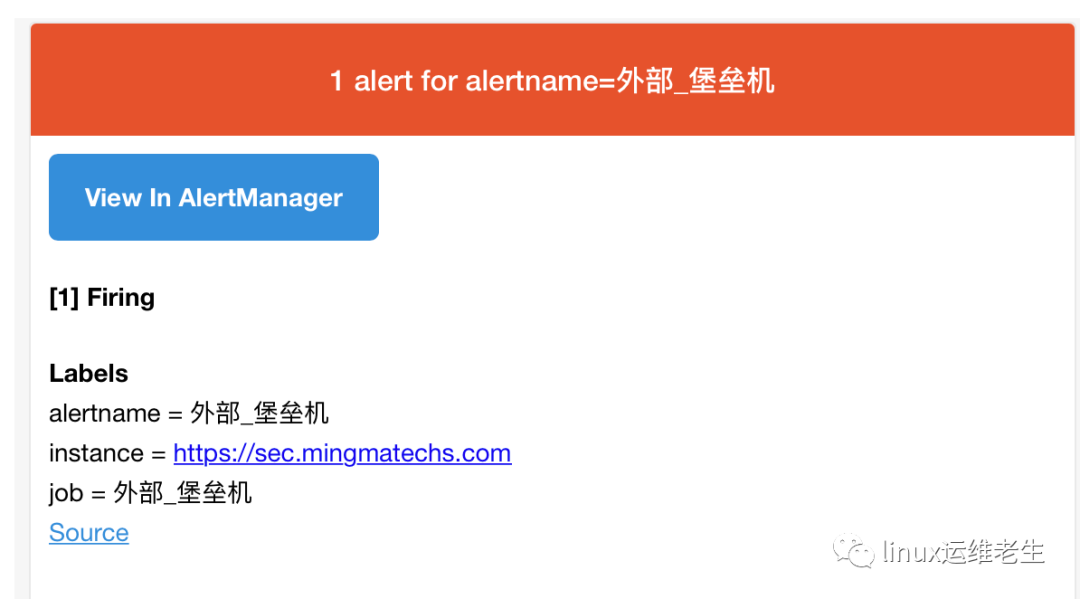
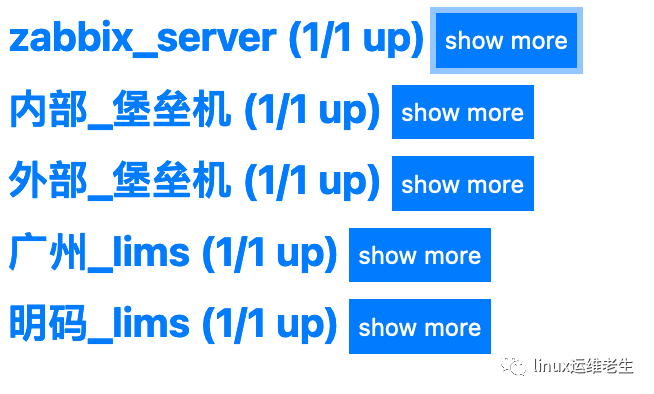
3. After the addition, I will post one example of the 5 sites I have monitored here.
4. I added a yml here
# Load rules once and periodically evaluate them according to the global 'evaluation_interval'.
rule_files:
- "first_rules.yml"
- "second_rules.yml"
- "third_rules.yml"
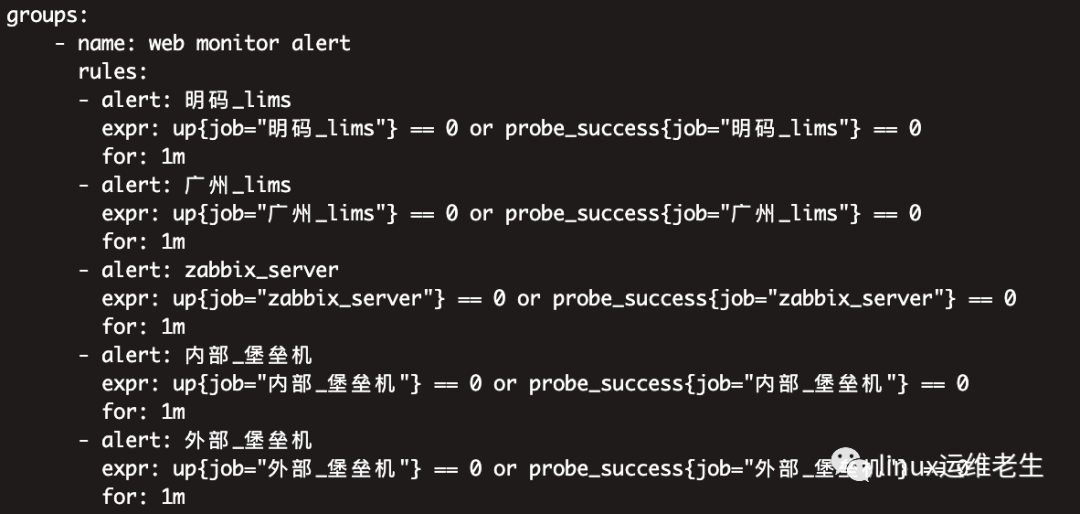
I added a third_rules.yml to the main configuration
Specific configuration
cat third_rules.yml
groups:
- name: web monitor alert
rules:
- alert: plaintext _lims
expr: up{job="clear_lims"} == 0 or probe_success{job="clear_lims"} == 0
for: 1m
- alert: Guangzhou_lims
expr: up{job="Guangzhou_lims"} == 0 or probe_success{job="Guangzhou_lims"} == 0
for: 1m
- alert: zabbix_server
expr: up{job="zabbix_server"} == 0 or probe_success{job="zabbix_server"} == 0
for: 1m
- alert: internal_bastion machine
expr: up{job="internal_bastion machine"} == 0 or probe_success{job="internal_bastion machine"} == 0
for: 1m
- alert: external_bastion machine
expr: up{job="external_bastion machine"} == 0 or probe_success{job="external_bastion machine"} == 0
for: 1m
5. Reload takes effect
supervisorctl update
supervisorctl restart prometheus_blackbox_exporter
curl -X POST http://localhost:9090/-/reload
3. Alarm test
1. http site test
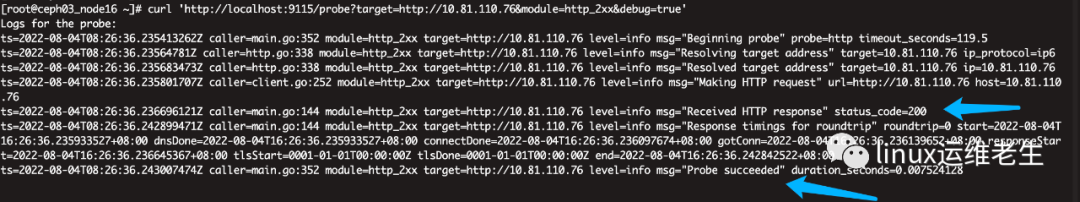
curl 'http://localhost:9115/probe?target=http://10.81.110.76&module=http_2xx&debug=true'
2, https site test
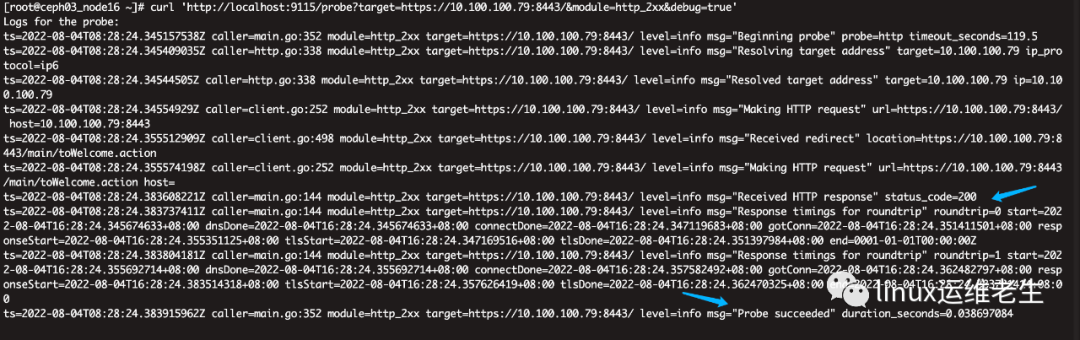
curl 'http://localhost:9115/probe?target=https://10.100.100.79:8443/&module=http_2xx&debug=true'
PS: The actual url address is this default will be forwarded to detect the specific or see the module posted below
https://10.100.100.79:8443/main/toWelcome.action
3. Specific use of Module configuration information
Module configuration:
prober: http
http:
ip_protocol_fallback: true
tls_config:
insecure_skip_verify: true
follow_redirects: true
enable_http2: true
tcp:
ip_protocol_fallback: true
icmp:
ip_protocol_fallback: true
ttl: 64
dns:
ip_protocol_fallback: true
recursion_desired: true
Fourth, the effect