0x01 Preface
Share some reports with no bounty for everyone to learn, why no bounty? Why publish it? Because it is either repeated or not accepted, it is intended to be published without any harm, maybe BugV, Hackeroneor Bugcrowd, without further ado, start my sharing , If it is used for illegal acts, the consequences will be at your own risk, and this public account will not be responsible!
0x02 v2rayN with Burpsuite
When overcoming the wall, the system's proxy has been set SSRPort, but we always need to test some websites that are blocked. How should we set the proxy? At this time, it is extremely stupid to set the proxy of Burpsuite to capture packets as the proxy of SSR! Because of this stupid practice, I have tried it, and it cannot be selected and used in Burpsuite proxy when SSR is turned on!
User options -> Connections -> Upstream Proxy Servers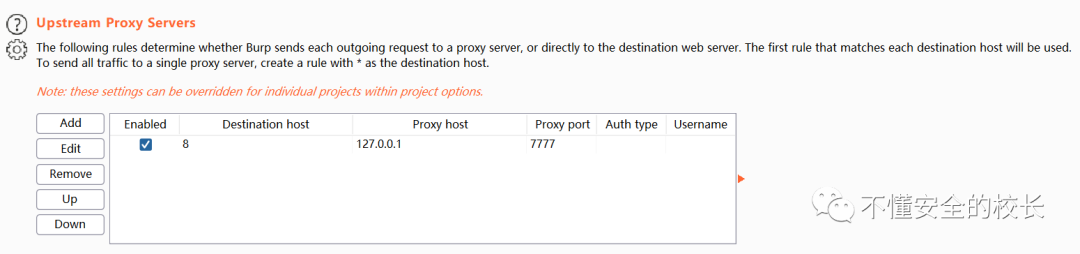 Click on the left
Click on the left Add, pop -up Add upstream proxy rulewindow, there are a total of eight setting items, we only need to fill in the first four.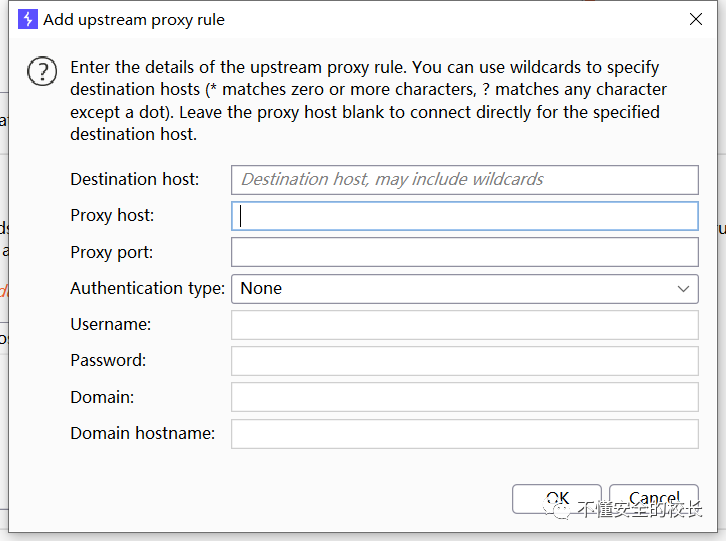
Add upstream proxy rule:
-
Destination host : * -
Proxy host: 127.0.0.1 -
Proxy port : v2rayN proxy port -
Authentication type : None 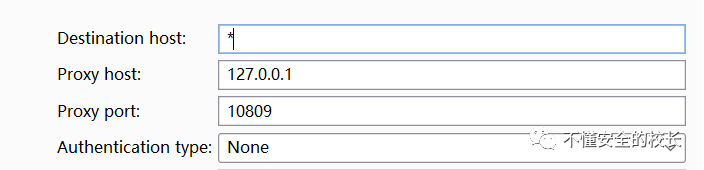 After completion, Burpsuite can start to capture the data packets of the blocked website. Does this belong to the
After completion, Burpsuite can start to capture the data packets of the blocked website. Does this belong to the Bug Bounty Tipcategory?
0x03 Enumeration by users who have forgotten their passwords
User enumeration can be achieved through the function of forgetting the password. When I retrieve the password, I enter the password casually, but it does not display the sending email, but prompts that the email is not registered. This prompt is convenient for us to blast and collect the email information of the users of the website, so as to facilitate the red team to prepare for the later social work. Some vendors accept this type of vulnerability, and the premise is that it is generally 100$-150$a bounty within this range. I'll show it again!
Manufacturer:Imgur @HackerOne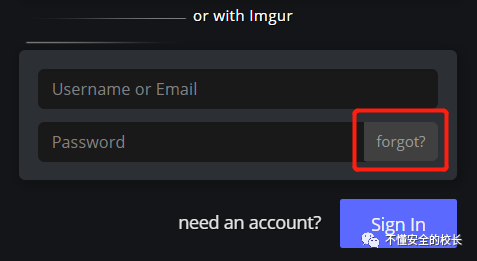 Follow the steps, we will find the password reset and enter any email address.
Follow the steps, we will find the password reset and enter any email address.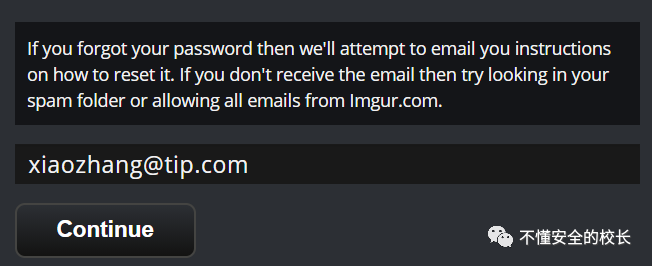
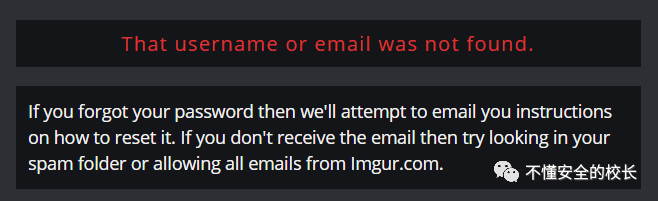 Tip: The username or email was not found. Yes, we found these kinds of bugs, but we
Tip: The username or email was not found. Yes, we found these kinds of bugs, but we Imgurdon't charge for them and the reports are ignored! Later I Hackeronefound that one of the vendors also had this kind of vulnerability, but repeated it and it passed me without any bounty.
My report is written like this: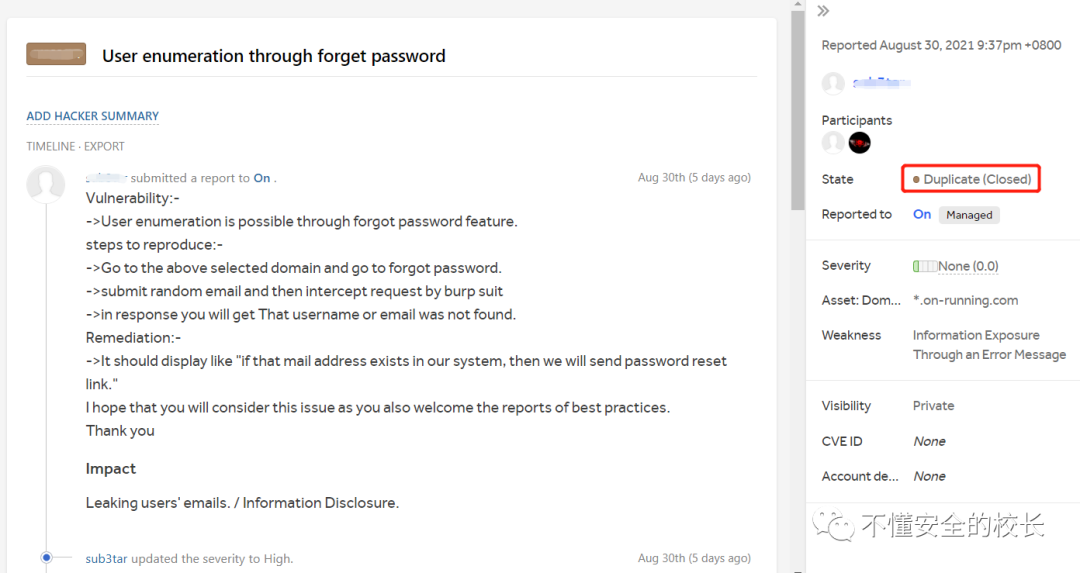
Vulnerability:-
->User enumeration is possible through forgot password feature.
steps to reproduce:-
->Go to the above selected domain and go to forgot password.
->submit random email and then intercept request by burp suit
->in response you will get That username or email was not found.
Remediation:-
->It should display like "if that mail address exists in our system, then we will send password reset link."
I hope that you will consider this issue as you also welcome the reports of best practices.
Thank you
Impact
Leaking users' emails. / Information Disclosure.
Although it BugVis repeated, the manufacturer gave me five points, but I don't know what it can be used for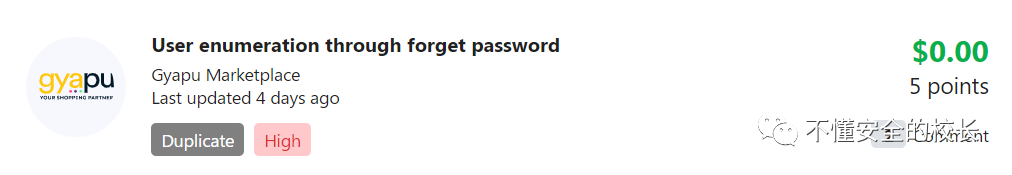
0x04 Open redirect
Unvalidated redirects and forwards can occur when a web application accepts untrusted input, which can cause the web application to redirect the request to a URL contained in the untrusted input. By modifying an untrusted URL input to a malicious site, an attacker could successfully launch a phishing scam and steal user credentials! Here @Owasp's an explanation about redirects that I copied from.
Share a Bug Bounty Tip:
Google Dork:site:example.com inurl:redir | inurl: URL | inurl:redirect | inurl:redirect | inurl:redirect | inurl:return | inurl:src=http | inurl:r=http
This Dork语句can effectively and quickly help us find related Open redirectvulnerabilities!
Manufacturer:Semrush @HackerOne
Using Burpsuiteprogress Fuzz, the dictionary can find very useful information collected by the masters on Github, which can help you quickly find the target vulnerability. 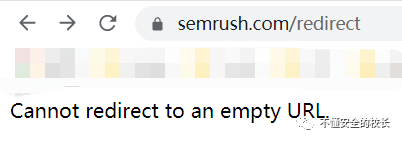 When I saw these in English I knew there was a drama! Continue to fuzz, try to find out the relative parameters, not long after I found it through Burpsuite,
When I saw these in English I knew there was a drama! Continue to fuzz, try to find out the relative parameters, not long after I found it through Burpsuite, 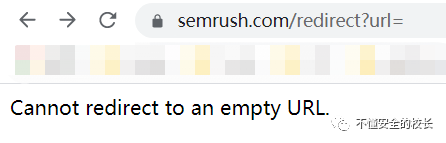 whether it can jump, I tried to input:
whether it can jump, I tried to input: http://www.baidu.comfound a successful jump, I began to check the vulnerabilities disclosed by the manufacturer to see if there were any repetitions. I found out that this hole was submitted by the big guy two years ago. I really wanted to ask the manufacturer why they didn't fix it. It gave me hope in vain!
HackerOne report:https://hackerone.com/reports/311330
If this type of vulnerability can be combined with XSS to prove the harm, the bounty is generally in 100$-500$this range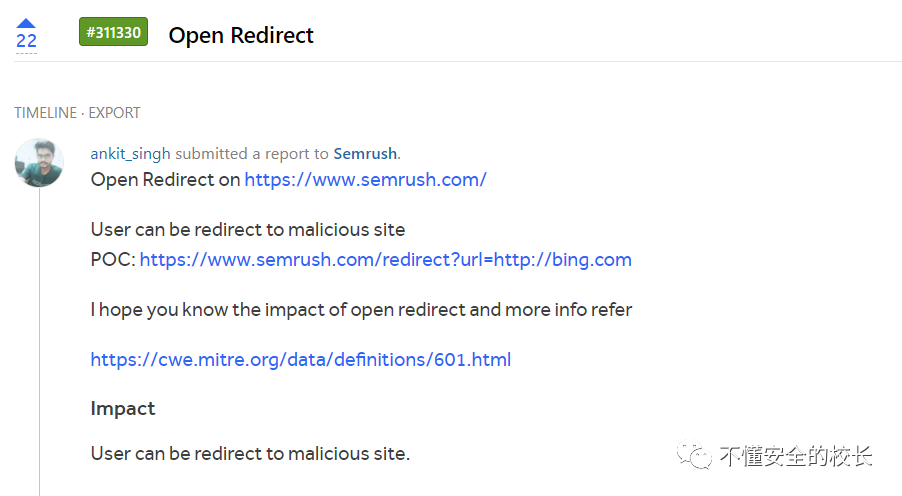
Open Redirect on https://www.semrush.com/
User can be redirect to malicious site
POC: https://www.semrush.com/redirect?url=http://bing.com
I hope you know the impact of open redirect and more info refer
https://cwe.mitre.org/data/definitions/601.html
Impact
User can be redirect to malicious site.
0x05 SQLi in Harvard Subdomain
Harvard's subdomain *.med.harvard.educan find many SQLi using Google Hacking syntax, I'll take one of them as an example
Use ffufor DirserchFUZZ the directory, and found that there is such a PHP file in the first-level directory. It is availability.php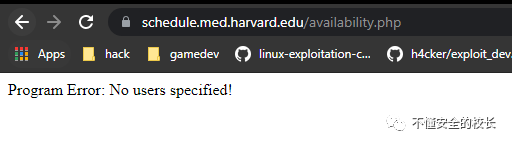 found that we are missing
found that we are missing usersparameters, let's fill it. 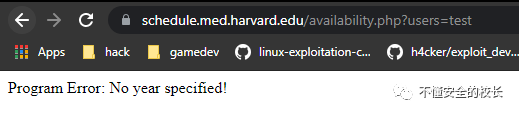 As before we need to supplement the parameters, and the same after! So I added a few parameters and got a web page!
As before we need to supplement the parameters, and the same after! So I added a few parameters and got a web page! 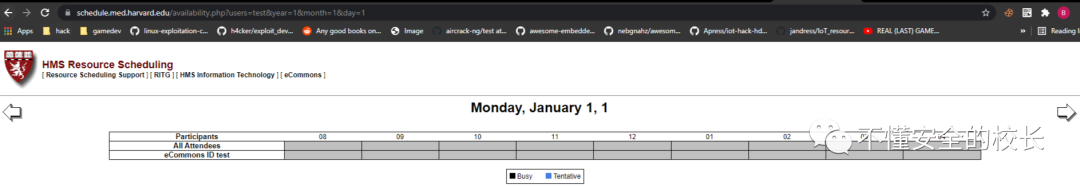 I
I Dayadded a 'prompt to the value of the parameter to report an error, we can get the result by running it with Sqlmap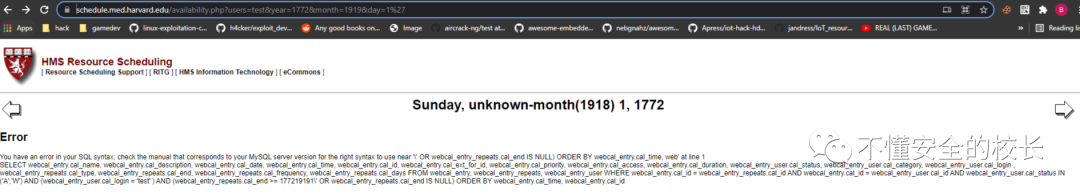
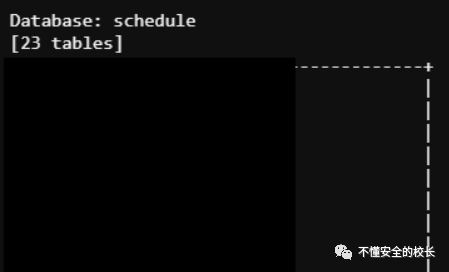 Unfortunately, there is no bounty platform for this domain name, so we alerted the school and asked them to fix the vulnerability. My friend
Unfortunately, there is no bounty platform for this domain name, so we alerted the school and asked them to fix the vulnerability. My friend @noob3xploiterwrote an article about this vulnerability and posted it on the Medium platform.
Medium:https://noob3xploiter.medium.com/sql-injection-in-harvard-subdomain-be67a5dbf664
0x06 end
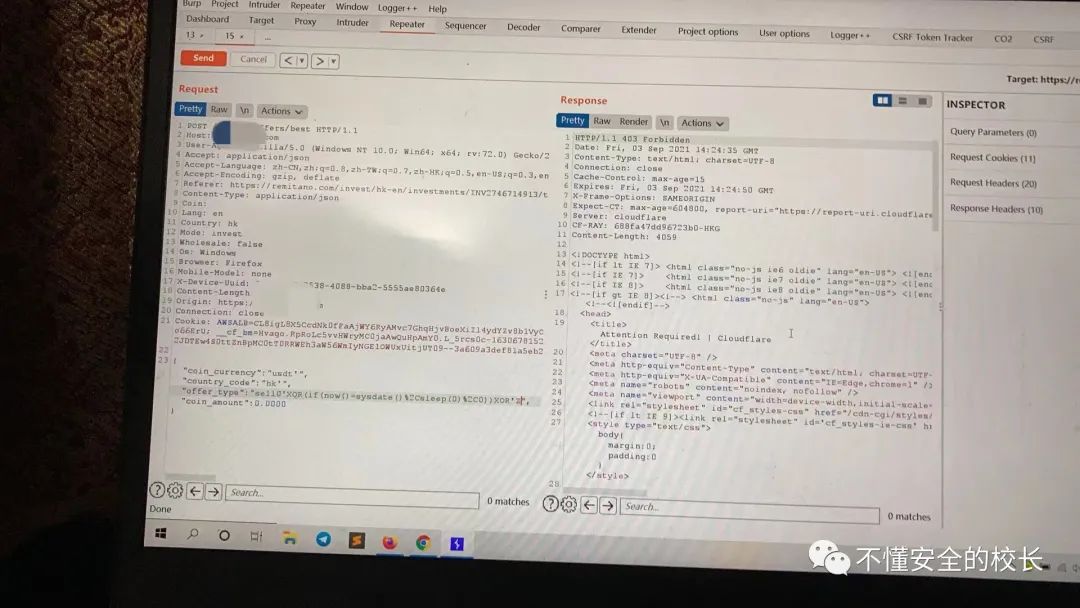 I would like to ask you masters,
I would like to ask you masters, Couldflarehow to bypass this foreign WAF? I look forward to the masters adding my WeChat and I will answer my questions for me, thank you very much!
If you have any questions about the article on the official account, you can contact the following WeChat:
