
System default permissions in Linux - umask
In the last lesson, we introduced umask: View the umask permissions of the current user;
Here I will add the umask -S option to everyone
Then the -S option will introduce you to
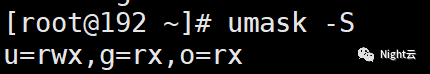
This is more user-friendly -S can be viewed directly
Default permissions - umask
· Assuming your umask is 003, what are the permissions of the created I add you and the directory under this umask?
Answer: umask is 003, so the removed permission is ---WX, so;
file: (-rw-rw-rw-)-(------wx)=-rw-rw-r--
Directory: (drwxrwxrwx)-(d----wx)=drwxrwxr--
· Ordinary user: 002
root: 022
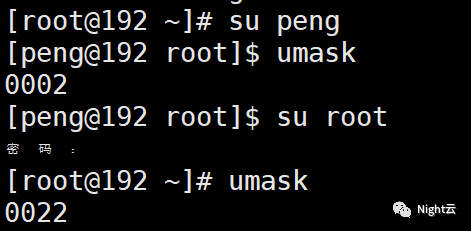
User and admin values are different
· Under what circumstances should umask be used?
Assuming that you and your colleagues are working on the same project in the same directory, if you use the default permissions of 0022, your colleagues will not be able to edit the files you create, so we can adjust the permissions to 0002.
Well, the default permissions of umask are finished. In the next section, we will talk about the special permissions of files - SUID SGID SBIT
SUID, get file owner and group permissions - only for files
GUID, even if it works on directories, it can also work on files
Act on file: same as SUID
Acting on directories: Inherit the parent set directory with groups - the directory will continue to inherit
SBIT means that only the owner of the file can delete and modify the file - only for directories
Both S and T are uppercase and lowercase
Capitalize Description: No X permission
Lowercase description: has X permission
SUID=4 SGID=2 SBIT=1

