
It is said that GitHub has suffered malicious attacks again, and this time there are more than 35,000 code bases affected?
This Wednesday, a software engineer Stephen Lacy suddenly tweeted: "I found that there is a wide range of large-scale malicious attacks on Github. At present, more than 35,000 code bases have been infected, ranging from Crypto (encryption), Golang, Python, js, bash, Docker, and k8s, etc., where malicious code is added to npm scripts, Docker images, and installation documentation."
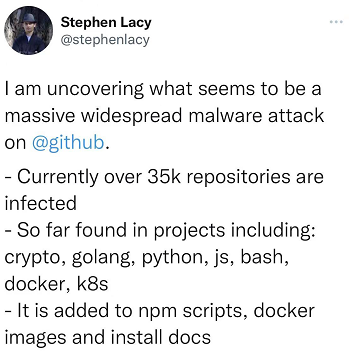
As soon as this news came out, the name of the code base that was very familiar caused the majority of developers to be quite shocked: what? Is there something wrong with so many official codebases? !

seemingly innocuous commit
From Stephen Lacy's personal introduction on Twitter, as a software engineer, he is mainly engaged in cryptography and open source, and he found the opportunity for this attack to review an open source project found through Google search.
"Most of these infected commits appear to be quite innocuous, usually with names like 'bump version to 0.3.11' that look like version updates." In addition, by examining the history of these repositories, Stephen Lacy found that Some commits are from project authors but not verified by GPG, and some are from users who do not exist yet.
(Note: GPG is the abbreviation of GNU Privacy Guard, which is a key-based encryption method that uses a pair of keys to encrypt and decrypt messages to ensure secure transmission of messages.)
Once developers use these repositories containing malicious code, their entire environment variables (ENVs) are leaked and uploaded to the attacker's server. ENVs include security keys, Amazon Web Services access keys, encryption keys and many more.
Hearing this, are the developers who use the libraries on GitHub such as Crypto (encryption), Golang, Python, js, bash, Docker and k8s a little nervous?
Rest assured, according to the technology website Bleeping Computer: "Actually those 35,000 projects were not affected or compromised in any way, and official projects such as Crypto (encryption), Golang, Python, js, bash, Docker, and k8s were also not affected." And those projects with malicious code are mostly forked or cloned versions of these official legitimate projects.

35k+ is not the number of infected codebases
In a tweet, Stephen Lacy also mentioned this: "Attackers will build fake codebase links and push clones of legitimate projects to GitHub to dump the blame on the original author of the codebase!"
After discovering the issue, Stephen Lacy quickly reported the issue to GitHub, urging it to search the codebase for the following malicious URLs:
hxxp://ovz1.j19544519.pr46m.vps.myjino[.]ru
Not only that, another developer James Tucker analyzed that the cloned codebase containing this malicious URL not only leaked the user's environment variables, but also contained a backdoor that would allow attackers to remotely install and run these malicious code in all Execute arbitrary code on the system.
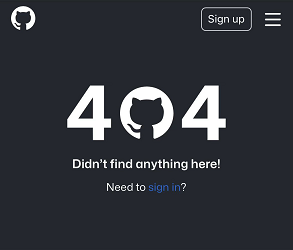
After searching for the URL on GitHub, Bleeping Computer found a total of 35,788 search results, i.e., the files contained malicious URLs - but this number is only the number of infected files, not the number of infected code repositories. Stephen Lacy also corrected this shortly after: The 35k+ infected on GitHub is the number of code snippets, not the codebase.
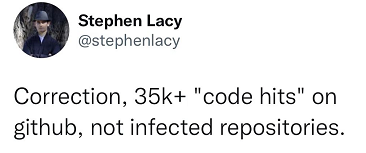
After further analysis, Bleeping Computer noted that of the 35,000+ files, the vast majority of cloned repositories were injected with malicious code sometime in the last month, with more than 13,000 search results from a site called Repository for "redhat-operator-ecosystem". However at the moment the library seems to have been removed from GitHub with a 404 (Not Found) error.
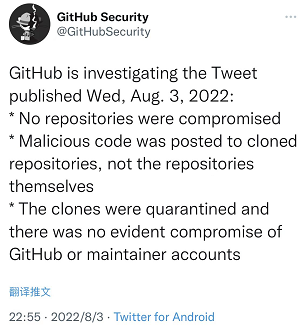
On the night of the incident, GitHub, which received Stephen Lacy's report, responded:
GitHub is investigating tweets posted on Wednesday, August 3, 2022:
*No repositories were compromised
*Malicious code was posted to cloned repositories, not the repository itself
*Those cloned repositories have been blocked and there is no apparent evidence that GitHub or maintainer account compromised
According to Bleeping Computer, Github has now removed most of the codebase containing malicious content after receiving reports of malicious incidents.

Authenticate with GPG key
Essentially, cloning open source projects on GitHub is a very common practice, and many developers even enjoy it. But this attack reminds us that it's best to use the project's official codebase, and beware of certain spoofed domains and cloned repositories, as they may just look the same as the original project, but hide malware in them.
Even more frightening is that some cloned repositories will continue to commit code under the original project author's username and email address, thus misleading other developers into thinking that the cloned repository's update commit was also made by the original project author , in exchange for trust.
So, as Stephen Lacy suggested on Twitter: "The best strategy for identifying fake commits is to use GPG keys for verification."
Reference link:
-
https://www.bleepingcomputer.com/news/security/35-000-code-repos-not-hacked-but-clones-flood-github-to-serve-malware/
-
https://news.ycombinator.com/item?id=32327903