This is the first time for me to come into contact with the knowledge of permissions, but I think this knowledge is very practical and interesting. Although I have written six sub-series of Linux basics, strictly speaking, the core of this series is three: The first is to learn the relevant instructions under Linux, which is the first step for us to get started with the Linux operating system; the second is the permission management under Linux that I want to write today; the third is the end of the next chapter, mainly A summary of the use of basic development tools in the Linux environment.
☁️: Topic 1: Classification of specific users in Linux
There are two kinds of users in Linux: super user (root) and ordinary user.
Super user: can do anything under the Linux system, the permissions are not controlled.
Ordinary users: Permissions are controlled and generally can only work in their own working directory (/home/xxx).
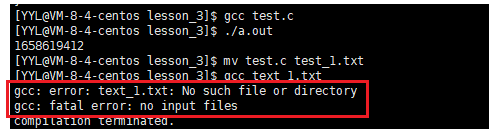
Command: su [username]
Function: switch user.
User switch:
root->normal user user: su user
Ordinary user -> root: su root (root can be omitted)
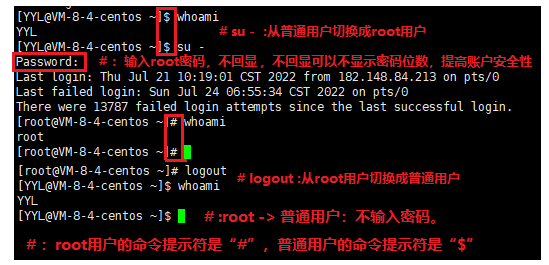
☁️: Note 1: Password Management
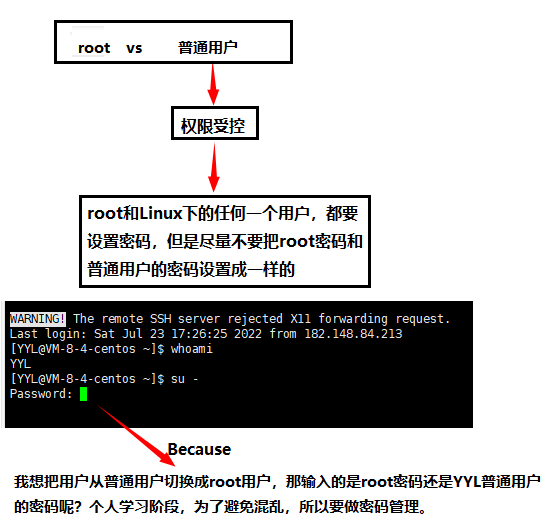
☁️: Note 2: What if I want to switch from my own user to someone else's user?
Method 1: As shown in the figure:
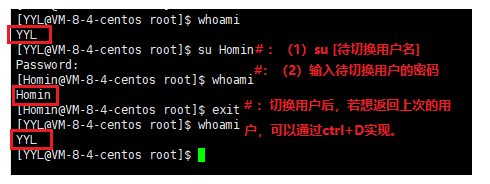
Method 2: Root users switch directly (password-free): su [user account to be switched]
☁️: Note 3: How to escalate the permissions of the current directive?
Suppose I only want to elevate the privileges of the current command and do not want to switch to the root user interface: for example, I try to change the account password of another normal user as a normal user, what should I do? ? ?
Syntax: sudo command
Function: Elevate the authority of the current command.
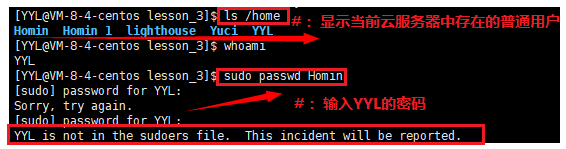
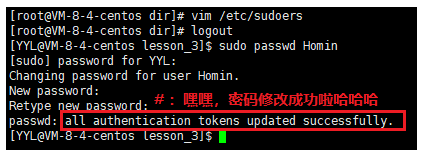
When we directly enter the above command and try to modify the password of the ordinary user Homin with the ordinary user YYL, the modification cannot be successful. The system will prompt us that YYL has not been added to the superuser (root) credit list, so the privilege of this command cannot be elevated. So to elevate the authority of the current command, you must first add ordinary users (YYL) to the trust list.
So: how do I add regular users to the trust list?
step1 : Switch to superuser; only superusers have the power to add regular users to the trust list.
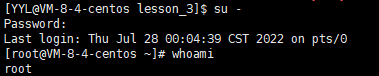
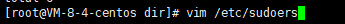
Step3: Slide down to the place shown in the pop-up file, and add the ordinary user (YYL) whose privileges are to be elevated to the trust list according to the format shown in the figure. (Note: first press: "i" to enter insert mode to add; after adding, press: esc key to enter the default mode, press "shift key +:", then press: "wq!" to save and exit, then press "ctrl +D" returns to the previous user YYL, and you can modify Homin's password as shown in step 4.)
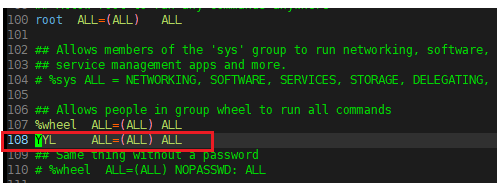
step4: as shown in the figure.
☁️: Topic 2: Linux Permission Management
Before starting the topic, let's think about a question: what is authority in real life?
☁️01 : Classification of file visitors (people)
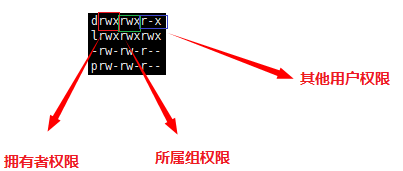
The classification of file visitors can divide users into three categories: the owner of the file (owner/User), the group to which the file belongs (Group), and the other users of the file (Others) . For a certain file, root and ordinary users can play multiple roles of the owner, the group they belong to, and other users. The two do not conflict, but complement each other. In addition, in Linux, all users must belong to a certain group. When this group is only you, the group will be named after your user name. The existence of the group to which it belongs is for more flexible permission configuration and to meet the function of team collaboration within the group. All users other than the file owner and the group they belong to are called Other.
☁️02 : File Type and Access Rights (Thing Properties)
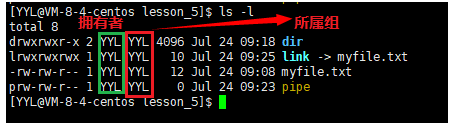
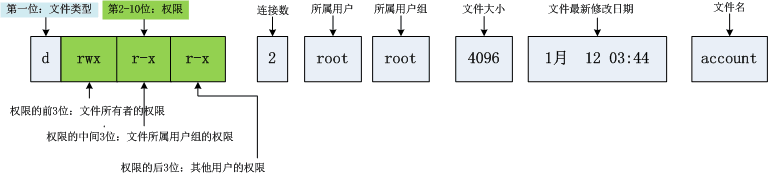
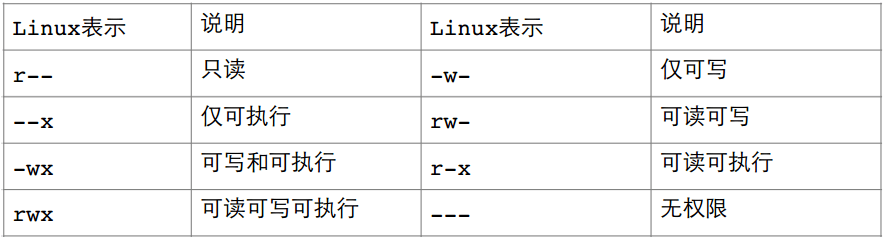
File = file content + file attribute; the file content can be viewed through the cat command, and the file attribute is shown in the figure. Permission types of files under Linux generally include read, write, and execute. The corresponding letters are r, w, x. Use the ll command to view file types and attributes.
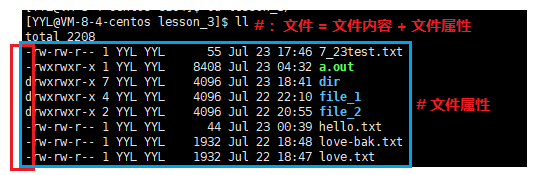
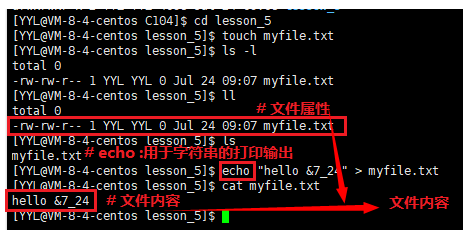


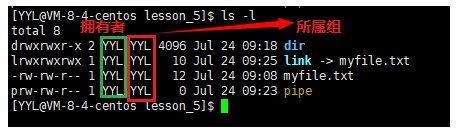
The file myfile.txt is a common file. The owner and group of the file are YYL, and they are both readable and writable. Other users of the file only have the right to read it. Other properties are shown in the figure below, so I won't go into details.
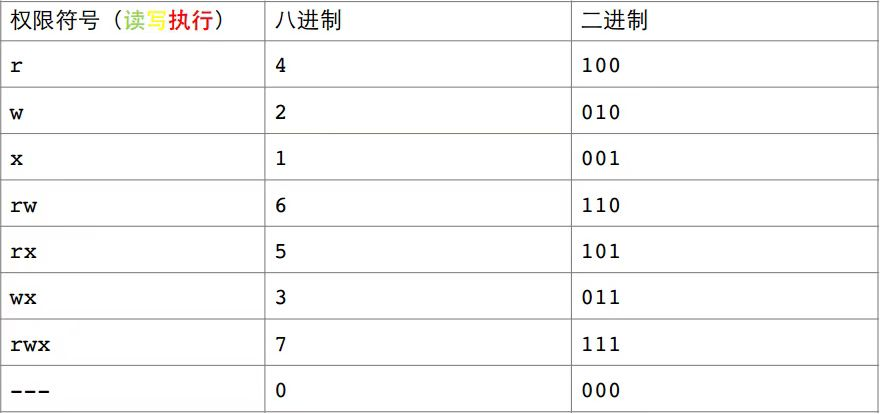
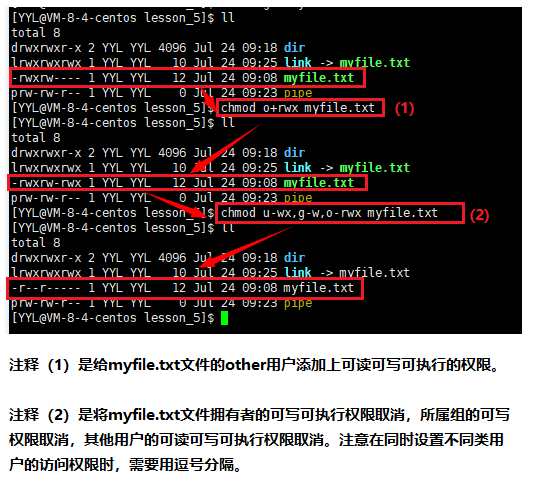
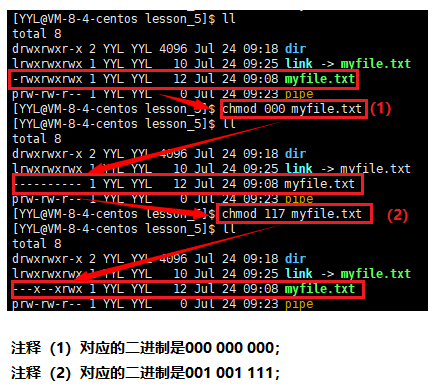
Permission change syntax : chmod option permission filename or directory name
Function : Set the access permission of the file. Common options : -R Recursively modify the permissions of directory files.
The chmod instruction modifies the format of the permission value (only the owner and root of the file can change the permission of the file, and ordinary users need to escalate the permission to modify the permission):
Format 1: User symbol +/-/= permission character
1) +: Add the permission indicated by the permission code to the permission scope.
How to change the owner (person) of a file
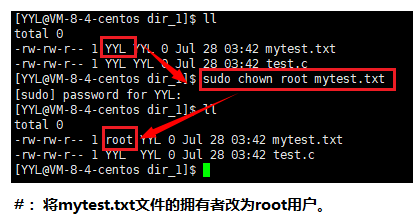
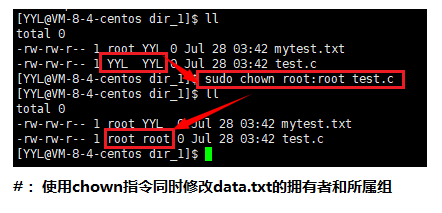
The command used to modify the owner of a file is chown. You need to switch to the root user to operate. If you are a normal user, you need to perform privilege escalation.
Syntax: chown option username file or directory name
Function: Modify the owner of the file.
Common options: -R Recursively modify the owner of directory files.
Examples are as follows:
How to change the group of a file
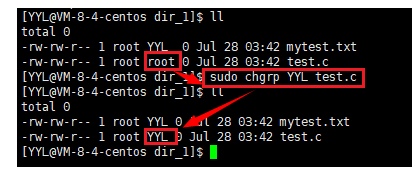
The command used to modify the group to which the file belongs is chgrp , and it is also necessary to switch to the root user or perform privilege escalation.
Syntax: chgrp options user name file name or directory name
Function: modify the group to which the file belongs.
Common options: -R Recursively modify the group that the directory file belongs to.
Examples are as follows:
☁️05 : mask: operation function: umask
umask is used to specify "the current user's default permission value when creating a new file or directory", and its function is to view or modify the mask of the file. When a new file is created, its initial permissions are determined by the file creation mask. Every time a user logs into the system, the umask command will be executed, and the mask will be automatically set to change the default value, and the new permissions will overwrite the old ones. umask "takes" the corresponding bits from permissions. The purpose of setting umask is to get what permissions the user needs when creating files.
Syntax: umask permission value
Function: View or modify the file mask.
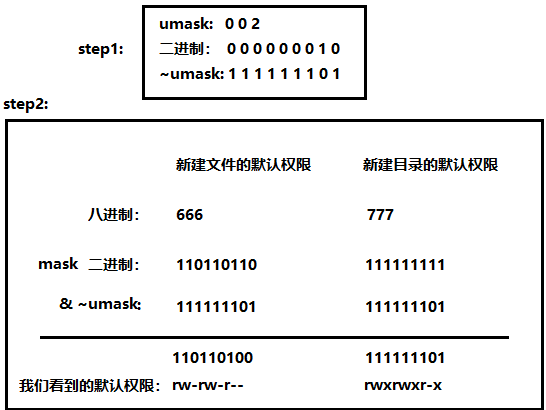
The default permissions for new folders are: 0666
The default permissions for new directories are: 0777
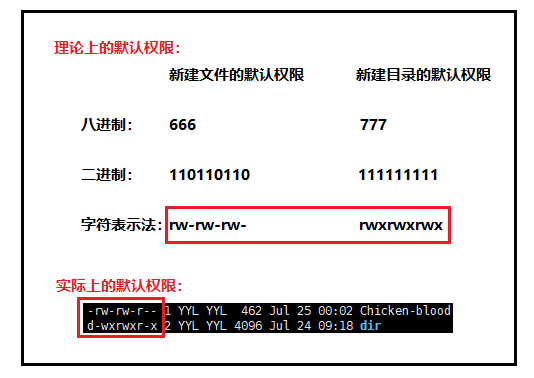
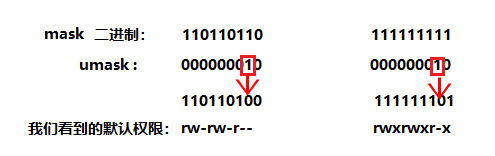
Why is the value of our newly created file or directory different from the theoretical default permission in practice? The reason is that it is also affected by umask when creating a file or directory . Assuming that the default permission is mask , the actually created file permission is : mask & ~umask.
Let's demonstrate that it is indeed umask that affects our final permissions.
Argument 1: Mathematical derivation:
Argument 2: Code Demonstration:
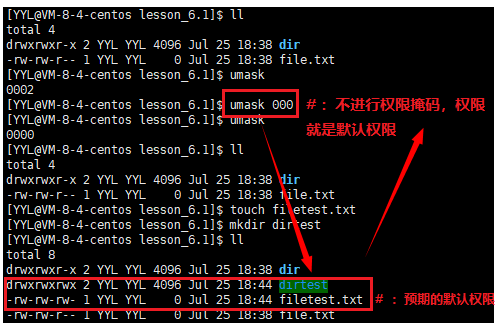
That is: any permission that appears in the permission mask should not appear in the final permission.
☁️06 : Permissions for directories (very important)
Everything under Linux is a file, and a directory is also a file. File = content + attribute, and the "attribute" of some files is stored in the directory, including the file name. For directories, readable and writable executables represent:
1) Read permission (r): If the directory does not have read permission, you cannot use commands such as ls to view the contents of the files in the directory.
2) Writable permission (w): If the directory does not have writable permission, you cannot create files in the directory and you cannot delete files in the directory.
3) Executable permission: If the directory does not have executable permission, you cannot cd into the directory.
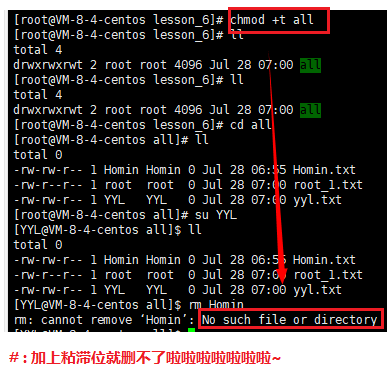
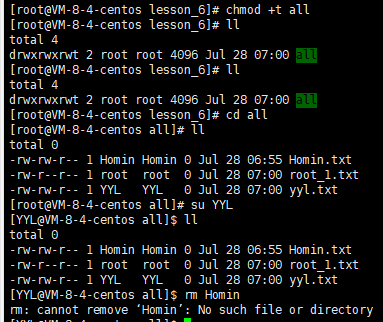
In this case, we think about a problem: there can be some directories under Linux, the owner and the group to which they belong are both root (or ordinary users), and others are allowed to create files in the directory as other, read, delete, and modify, etc. Does that mean that as long as the user has the write permission of the directory, the files in the public directory can be deleted at will, regardless of whether the user has the write and read permission of the file? The answer is: yes, let's take a look at the process:
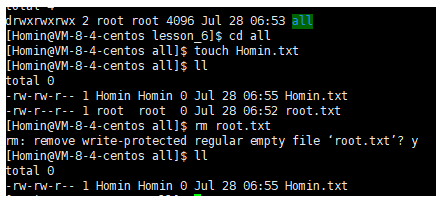
We can see that the ordinary user Homin deletes the file root.txt in the shared directory that does not belong to him, which is obviously very unreasonable. To solve this unreasonable problem, we can add the sticky bit to the shared directory.
grammar:
Function: Add sticky bit to directory.